PayPal Has Updated Its Webhook Verification Endpoint
Jun 01, 2023
4 min read

TL;DR;PayPal requires that all the webhook notification messages it sends be verified by the webhook listener receiving these messages.
This requirement enhances security by ensuring that your webhook listener is receiving authentic PayPal webhook messages.
PayPal has updated its endpoint for verifying PayPal webhook notification messages, and its old webhook verification method is now deprecated. The updated endpoint simplifies the process of verifying PayPal webhook messages, which improves the developer experience.
The update also incorporates a lot more of our REST APIs (such as the Orders API). You may learn more about the updated rationale here.
A webhook is an automated HTTP request sent from an application when triggered by an event. This request carries a message (called a payload) to a unique destination URL (called a webhook listener), and the receiving application can take further actions based on the payload content. Webhooks allow applications to communicate seamlessly with each other and enable speed in processing and service delivery.
PayPal’s REST APIs use webhooks to notify your application that an event has occurred; for example, a new order has been placed, or a payment has been processed. You can create a webhook associated with an event in your PayPal Developer Portal account. PayPal webhooks support an extensive list of event types.
An unscrupulous player could spoof a webhook notification message and attempt to make the message appear as if it originated from PayPal. Therefore, to ensure security, PayPal requires that applications verify all webhook notifications received from PayPal.
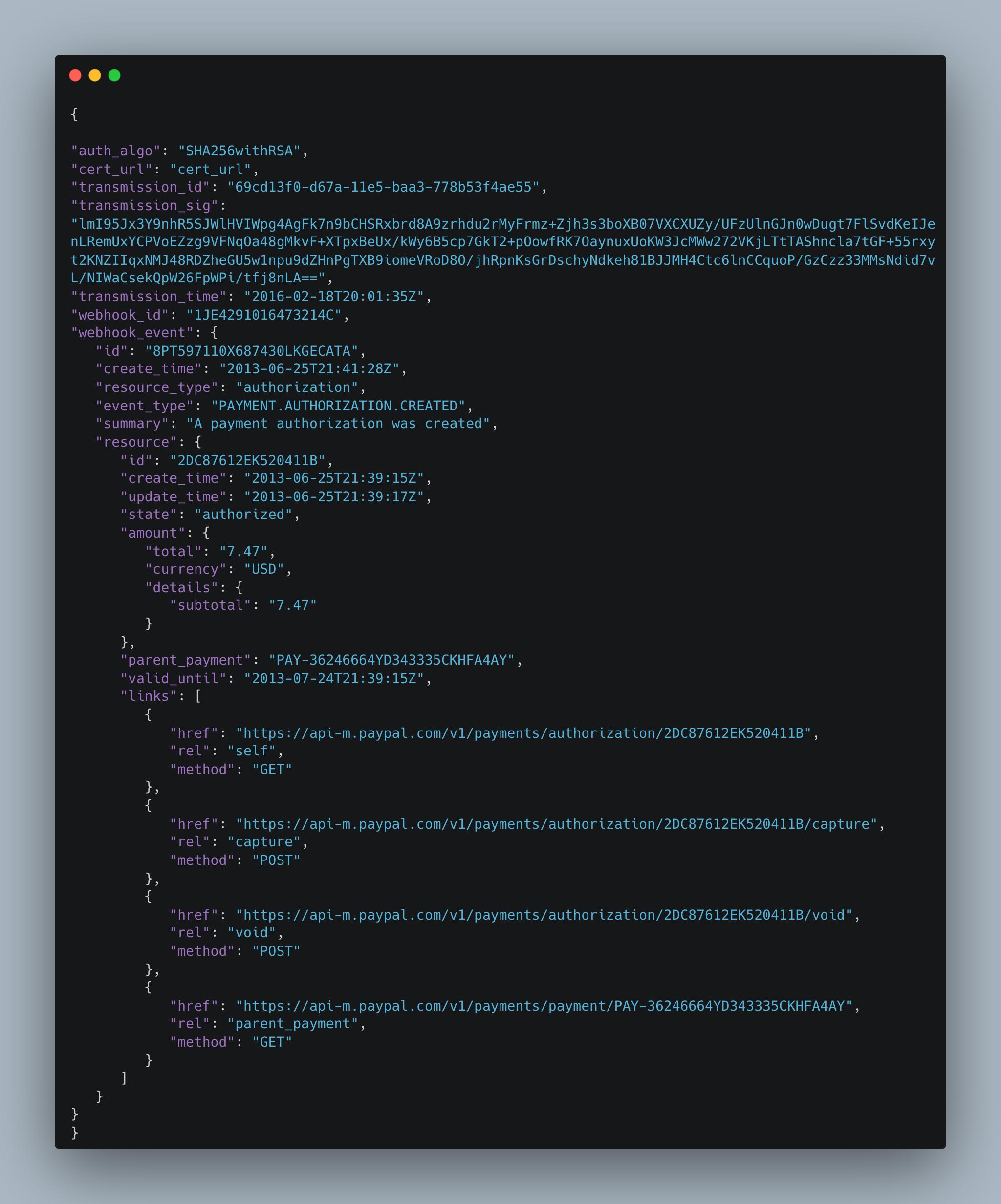
To verify the PayPal webhook message, your application sends a POST request to PayPal’s verify-webhook-signature endpoint with a payload containing several required parameters:
- auth_algo extracted from the PAYPAL-AUTH-ALGO value in the webhook response header.
- cert_url extracted from the PAYPAL-CERT-URL value in the webhook response header.
- transmission_id extracted from the PAYPAL-TRANSMISSION-ID value in the webhook response header.
- transmission_sig extracted from the PAYPAL-TRANSMISSION-SIG value in the webhook response header.
- transmission_time extracted from the PAYPAL-TRANSMISSION-TIME value in the webhook response header.
- webhook_id The ID of the webhook as configured in your PayPal Developer Portal account.
- webhook_event This is the webhook notification response received from PayPal, which you are now verifying.
Here is a sample webhook verification payload:
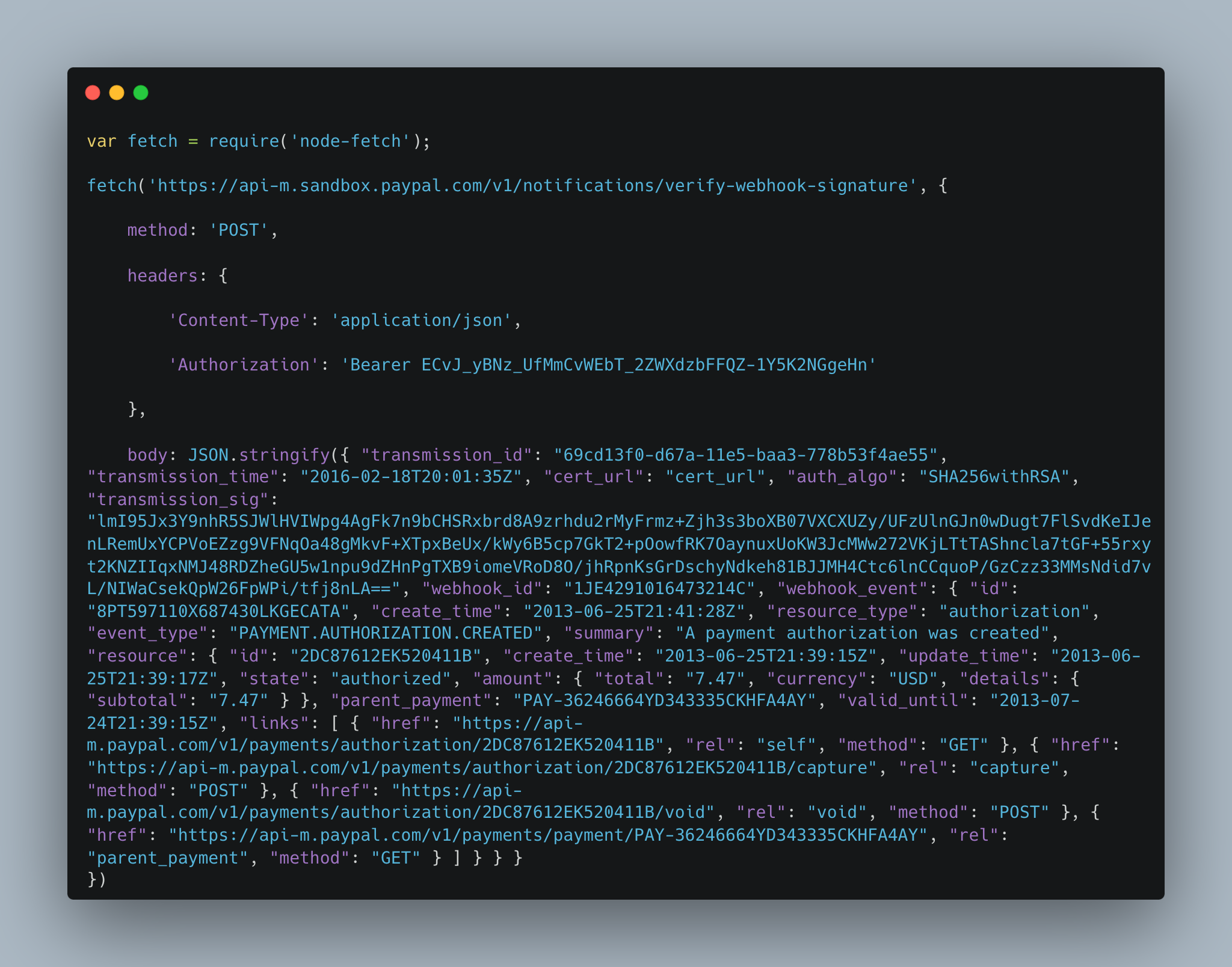
Here is a sample POST request verifying a PayPal webhook notification, sent from a NodeJS application:
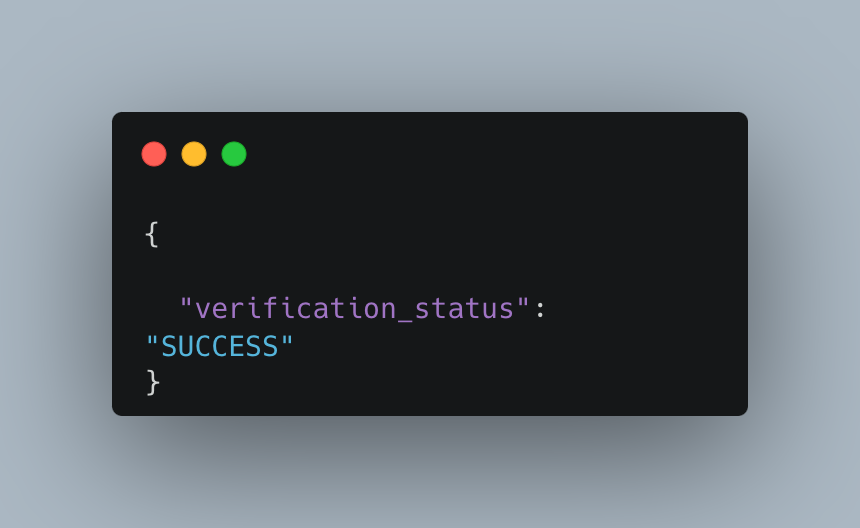
When your webhook verification request is successful, PayPal responds with the following payload (and an HTTP status of 200):
PayPal has a webhook simulator with which you can quickly test your webhook listener. Grab the URL of your webhook listener, or grab a mock listener URL from services like https://webhook.site. In the webhook simulator, enter this URL in the Webhooks URL field, select the Event Type for which you want a notification message, then click Send Test:
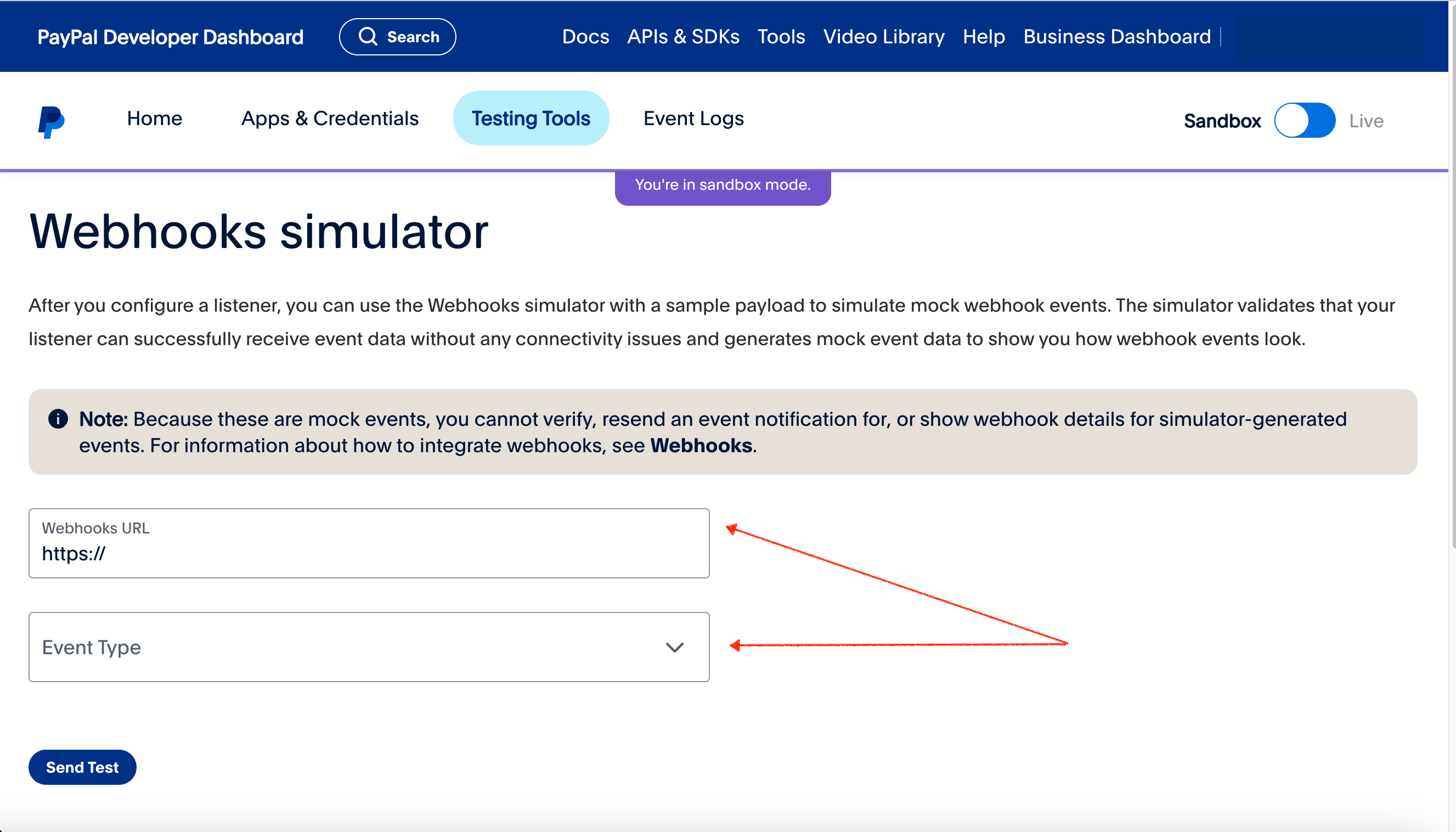
Your webhook listener should receive a mock payload from PayPal that resembles the examples provided earlier in this post.
PayPal takes the security of our products very seriously; with this update to our webhook verification endpoint, we continue to provide seamless payment integrations, coupled with mission-critical quality security standards.
Join the PayPal Developer Community!
Our Developer Community members support each other in integrating PayPal technologies, contributing to open source, expanding knowledge and networks, and improving PayPal’s products and documentation. We’d love to have you join us! 💙
Recommended

PayPal No-Code Estimates: Get on the Same Page!
4 min read

Accept E-Commerce Payments Easily with PayPal’s Buttons Component
9 min read
