Secure Your API Credentials
Apr 22, 2025
8 min read
Imagine you're about to head out for a weekend getaway and, feeling a bit too confident, you tuck your house keys under the doormat. You figure, "Who’s really going to check there?" But then your nosy neighbor swings by, spots the keys, and suddenly they’re rummaging through your fridge and swiping your TV.
That’s basically what happens when you don’t secure your API credentials. They’re like the credentials to your digital kingdom, if someone gets their hands on them, they can stroll right in and make off with your data, services, and even your reputation.
Just like you wouldn’t leave your house keys in plain sight, you shouldn’t leave your API credentials exposed either. These little digital credentials grant access to all sorts of sensitive information, from user data to payment systems, and even control over your app’s functionality. Forgetting to properly secure them is like putting a sign on your front door that says, “Come on in, everything’s free for the taking!” To keep your API credentials safe, you need to follow a few simple yet effective practices, because the last thing you want is a hacker lounging on your digital couch, bingeing through your sensitive data like it’s their favorite show.
Let’s dive into the best ways to lock up those credentials and keep the digital thieves at bay.
What are API credentials and what are they used for?
An API, or Application Programming Interface, is a set of rules and protocols that allows different software applications to communicate with each other. It defines the methods and data formats that applications can use to request and exchange information. APIs are essential for integrating different systems and enabling them to work together seamlessly.
An API credential is a unique identifier used to authenticate a user or system making a request to an API. Essentially, it acts as a digital “password” that grants access to specific services or data provided by an API. API credentials are essential for verifying that the person or application making the request has the proper permissions to interact with the API. They are widely used in web development, especially when integrating third-party services, such as payment gateways or data storage solutions. For example, PayPal's REST APIs require an API credential to securely process payments or access customer information. By using an API credential, developers ensure that requests are authenticated, and that sensitive data is protected. If you're looking to explore how PayPal uses API credentials for their REST APIs, you can check out the official PayPal API documentation for detailed information.
API credentials serve as the main mechanism for controlling access to APIs, helping to prevent unauthorized usage and ensuring secure communication between systems.
How do API credentials work?
API credentials work as a secure means of authenticating and authorizing users or systems making requests to an API. In technical terms, when a developer integrates an API into their application, they receive a unique API credential from the API provider (such as PayPal, Google, or others).
The credentials are not included with the HTTP request, as they are designed to be long-lived. The application utilizes these long-lived credentials to obtain a short-lived, temporary token (access token), which serves to authenticate with the server. This token is never transmitted as a query parameter because such parameters are not encrypted, making them vulnerable to interception by anyone with network access. Instead, the tokens are transmitted in a secure header, which is encrypted through the HTTPS connection.
Behind the scenes, the API server receives the request, extracts the API credential, and cross-references it with its database to verify if the credential is valid and associated with the correct permissions. If the API credential is valid and has the necessary access rights, the server processes the request and returns the requested data or action. If not, the server denies access, often with an error message.
How to use API credentials?
API credentials should always be kept secure and used carefully to prevent unauthorized access. In general, how to use API credentials involves securely storing the credentials and including them in your API requests, typically in the request header (Authorization header or a session cookie). It’s important to never expose the API credentials in public-facing code or share it openly, as this could lead to unauthorized usage or security vulnerabilities.
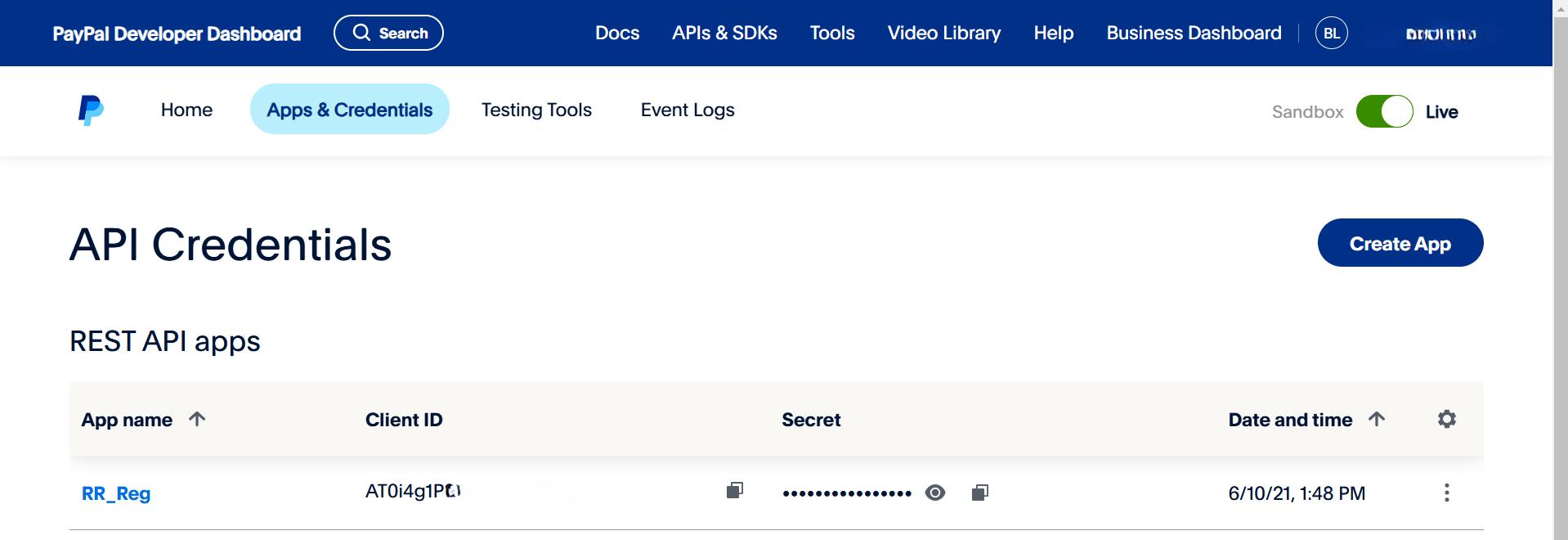
In PayPal, API credentials are used to authenticate requests to their various APIs, such as the PayPal REST API, which enables payment processing and account management.
For example, developers need to retrieve their API credentials from the PayPal Developer Dashboard and include the API credentials in the authorization header for each API request.The application encodes the CLIENT_ID and CLIENT_SECRET into a base64 format and includes this information in the Authorization header of a login request to an endpoint such as api.paypal.com/v1/oauth2/login. The server responds with a temporary token, which is used for subsequent API calls. This approach helps to prevent the need to transmit the long-lived secret with every API request.
It's also essential to note that different PayPal APIs, such as the REST API and the NVP/SOAP APIs, may have different methods for API credentials usage, with the REST API typically using client IDs and secret credentials, while older APIs might rely on different authentication mechanisms. OAuth is the standard method for authorization. Please note that older API types may use outdated and deprecated methods.
Regardless of the specific API, it’s crucial to follow best practices for security, including rotating credentials periodically and using secure methods like storing in dedicated secret storage systems such as KMS services which exist in every Content Security Policy.
Are API credentials secure?
While API credentials are a useful tool for authenticating requests, they are generally not considered secure when used alone. If someone gains access to the API credentials, they can potentially misuse it, leading to unauthorized access to sensitive data or services.
To make API credentials more secure in practice, several measures are commonly implemented. First, using HTTPS (SSL/TLS encryption) ensures that API credentials are transmitted securely over the network, preventing interception by attackers.
Another common approach is OAuth authentication, which requires users to authorize access to specific resources rather than simply providing static API credentials.
OAuth is a delegation-based authorization framework that is preferable to static API keys when accessing user data or resources across different applications. It is particularly beneficial when user experience and security are priorities, as it prevents the exposure of user credentials and facilitates easier management of permissions and access.
Furthermore, credentials rotation, especially where API credentials are regularly updated can help minimize the risk of abuse if a credentials is compromised.
Combining these practices with strong security controls ensures that API credentials are more resilient against potential threats.
How to store API credentials securely
When it comes to how to store API credentials securely, it’s crucial to follow best practices to minimize the risk of exposure.
Where to store API credentials is a key consideration. Never hard-code them directly into your source code or commit them to version control. Instead, use environment variables or a secrets management service (such as AWS Secrets Manager or HashiCorp Vault) to securely store credentials.
API credentials management should include access control measures, ensuring that only authorized users or systems can retrieve the credentials. For applications with multiple users, implement proper access control by assigning specific permissions based on the principle of least privilege, allowing users to access only the credentials they need.
Additionally, in code, ensure that API credentials are not exposed in public repositories, log files, or error messages. For secure API credentials authentication, consider using libraries or frameworks that handle credentials management safely and avoid storing credentials in unencrypted formats.
API credentials rotation is another critical aspect of API credentials security. Regularly refresh credentials to minimize the window of exposure if a credentials is compromised. Establish a process for rotating credentials and ensure that old credentials are deleted from all systems once they're no longer in use.
This should also include a clear policy for revoking access in case a credential is compromised.
Lastly, investing in training and development for your team is vital to ensure everyone understands the risks associated with API credentials management and is familiar with secure coding practices. Regularly educating your team about best practices for handling sensitive data, such as API credentials, will help mitigate security risks and ensure robust protection across your systems.
Frequently asked questions about APIs
Can you share API credentials securely?
While you can share API credentials, it carries risks, especially if not done securely. To share API credentials securely, always use encryption and secure communication protocols like HTTPS. Avoid sharing credentials through unencrypted methods like email. Instead, use secure systems such as encrypted vaults (e.g., AWS Secrets Manager) to share credentials. Additionally, limit credentials permissions and rotate credentials regularly to reduce the impact of any potential compromise.
Do API credentials expire?
Yes, API credentials can expire. The expiration depends on the API provider and the type of credentials. For PayPal, API credentials expire after 3 years. After this period, a new certificate must be generated. Other credentials, like client IDs and secret credentials, generally don’t expire but should be rotated periodically for security. It's important to monitor your credentials and renew them on time to avoid service interruptions.
What are audit logs?
Audit logs and monitoring play a crucial role in maintaining the security of credentials. By tracking how credentials are used and flagging any unusual activity, organizations can quickly identify and respond to potential security threats. This proactive approach helps ensure that credentials are not misused, and that any suspicious behavior is promptly addressed, thereby enhancing overall security.
Recommended

Developer Day for Fastlane by PayPal: A Masterclass of Innovation
5 min read
Pay by Bank for E-Commerce | Using Bank Accounts to Make Purchases with SMBs [SEPA]
5 min read

PayPal Dev Days 2025: Building Smarter Commerce
5 min read